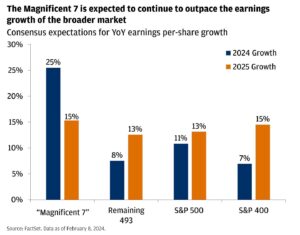
The tech sector braces for a pivotal week as industry giants prepare to release their third-quarter earnings reports, setting the tone for broader market movements. With companies like Microsoft, Meta, and Alphabet scheduled to unveil their financial performance, investors and analysts alike are keeping a close watch on these bellwether stocks. These reports come at a crucial time, as the technology sector grapples with persistent inflation concerns, shifting consumer behavior, and ongoing supply chain challenges. In an era dominated by digital transformation, businesses are increasingly recognizing the paramount importance of maintaining robust cybersecurity measures. This comprehensive approach encompasses various strategies, tools, and protocols designed to safeguard sensitive information and protect against potential threats.
Organizations must first establish a solid foundation by implementing multi-layered security protocols. This includes advanced firewalls, encryption methods, and regular security audits to identify vulnerabilities. Employee training programs play a crucial role, as human error remains one of the primary vectors for security breaches.
Modern cybersecurity frameworks incorporate artificial intelligence and machine learning algorithms to detect and respond to threats in real-time. These systems analyze patterns, identify anomalies, and automatically initiate countermeasures when suspicious activities are detected. This proactive approach significantly reduces response times and minimizes potential damage.
Data encryption serves as a fundamental component of any security strategy. Organizations must ensure that both data at rest and in transit are properly encrypted using industry-standard protocols. This includes implementing end-to-end encryption for communication channels and secure storage solutions for sensitive information.
Access control mechanisms represent another critical aspect of cybersecurity. Organizations should adopt the principle of least privilege, ensuring employees only have access to resources necessary for their specific roles. Multi-factor authentication adds an extra layer of security, requiring users to verify their identity through multiple methods before gaining access to sensitive systems.
Regular security assessments and penetration testing help identify potential vulnerabilities before malicious actors can exploit them. These tests simulate real-world attack scenarios and provide valuable insights into system weaknesses that require attention.
Incident response plans must be well-documented and regularly updated to address evolving threats. These plans should outline specific procedures for different types of security incidents, including data breaches, ransomware attacks, and social engineering attempts. Regular drills and simulations ensure team members understand their roles and responsibilities during security events.
Cloud security has become increasingly important as organizations migrate their operations to cloud platforms. Implementing proper security controls, monitoring tools, and compliance measures for cloud environments is essential for protecting data and applications hosted in the cloud.
Regulatory compliance also plays a significant role in cybersecurity strategies. Organizations must stay current with relevant industry regulations and data protection laws, implementing necessary controls to ensure compliance while protecting sensitive information.
the importance of regular backups cannot be overstated. Organizations should maintain secure, encrypted backups of critical data and systems, regularly testing restoration procedures to ensure business continuity in the event of a security incident.
Modern cybersecurity requires a holistic approach that combines technical solutions with proper policies, procedures, and employee awareness. As threats continue to evolve, organizations must remain vigilant and adaptable in their security strategies to protect against emerging risks and maintain the trust of their stakeholders.